Endpoint Security Market Growth: Safeguarding Data Integrity
Strong 8k brings an ultra-HD IPTV experience to your living room and your pocket.
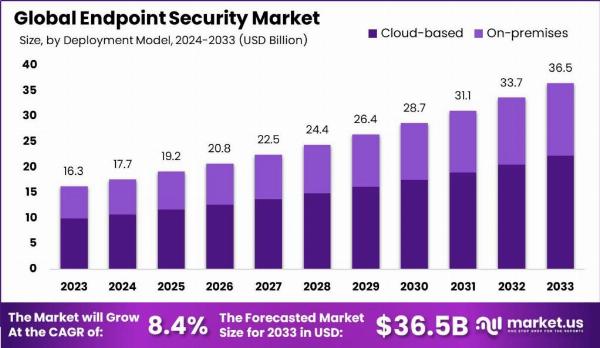
Endpoint security is a critical component of cybersecurity that focuses on protecting devices such as computers, smartphones, and tablets from various online threats. As our reliance on digital devices grows, so does the need to ensure they are secure from potential cyber attacks. The endpoint security market has seen substantial growth as businesses and individuals alike prioritize safeguarding their sensitive data and maintaining the integrity of their digital operations.The Endpoint Security Market is projected to reach approximately USD 36.5 billion by 2033, with a steady Compound Annual Growth Rate (CAGR) of 8.4%. In 2023, it was estimated to be worth USD 16.3 billion.
Growth Factors:
One of the primary growth factors is the increasing frequency and sophistication of cyber attacks targeting endpoint devices. Hackers constantly evolve their methods to exploit vulnerabilities in devices and networks, prompting organizations to invest in robust endpoint security solutions. Moreover, the proliferation of remote work and bring-your-own-device (BYOD) policies has expanded the number of endpoints that require protection, further driving market growth. Additionally, regulatory compliance requirements mandate organizations to implement effective endpoint security measures to protect sensitive information and avoid legal penalties.
Read more @https://market.us/report/endpoint-security-market/
Emerging trends:
Emerging trends in the endpoint security market include the integration of advanced technologies such as artificial intelligence (AI) and machine learning (ML). These technologies enhance the capability to detect and respond to threats in real-time, improving overall security effectiveness. Moreover, the shift towards cloud-based endpoint security solutions offers scalability and flexibility, enabling organizations to adapt their security measures more dynamically to changing business needs and evolving threat landscapes.
Appications:
- Endpoint security finds applications across various sectors and scenarios. In corporate environments, it ensures the protection of sensitive business data accessed through employee devices.
- In healthcare, it secures patient information stored on medical devices and computers. Government agencies use endpoint security to safeguard classified data on devices used by personnel.
- These diverse applications underscore the critical role of endpoint security in safeguarding data across different industries and sectors.
Challenges:
The endpoint security market faces several challenges. Managing a large number of diverse endpoints distributed across different locations can be complex and resource-intensive for organizations. The rapid evolution of cyber threats necessitates continuous updates and patches to security protocols, which can strain IT resources and budgets. Moreover, the complexity of integrating and managing multiple security solutions across various endpoints poses operational challenges for businesses.
Opportunities:
There are significant opportunities for growth in the endpoint security market. Businesses are increasingly seeking integrated security solutions that offer comprehensive protection across all endpoints and network environments. The proliferation of Internet of Things (IoT) devices further expands the scope of endpoint security, creating new opportunities for innovation and market expansion. By addressing these opportunities and challenges effectively, organizations can strengthen their cybersecurity posture and mitigate the risks associated with cyber attacks.
In conclusion, endpoint security plays a crucial role in protecting devices and data against a wide range of cyber threats in today's digital landscape. As the reliance on digital technologies continues to grow, so will the demand for robust endpoint security solutions. By leveraging emerging trends, addressing challenges, and capitalizing on opportunities, businesses can enhance their cybersecurity defenses and safeguard their sensitive information effectively.
Note: IndiBlogHub features both user-submitted and editorial content. We do not verify third-party contributions. Read our Disclaimer and Privacy Policyfor details.


