 White Hat Link Building – Safe. Powerful. Long-Term.
White Hat Link Building – Safe. Powerful. Long-Term.
ERROR, DEFECTS, BUGS, AND INCIDENTS- HOW ARE THEY DIFFERENT?
Written by Lucia Adams » Updated on: November 19th, 2024
With the age of artificial intelligence digging deep into the veins of organizational procedures; it is time for businesses big and small to address the cybersecurity challenges with finesse. Talking of cyberthreats, the world has witnessed vicious security and data breaches that have accounted for massive losses. Timely software testing has become an indispensable task that needs to be performed periodically. These help in identifying the loopholes in cybersecurity lineage across the organizational thread.
“IoT cyberattacks are expected to double by 2025”
Embroker
Cybersecurity adapts to the evolving cyberthreats. Phishing attacks, ransomware, social engineering attacks, credential theft, or stolen or compromised devices are some of the common cyberthreats that the business landscape is fighting. Another score from Accenture presents a grim situation of the cybersecurity landscape worldwide.
“43% of cyberattacks are aimed at small businesses, but only 14% are prepared to defend themselves”
Accenture’s Cost of Cybercrime Study
With these startling numbers in place, it will be highly beneficial for all cybersecurity aspirants to make a beginning in a thriving cybersecurity career trajectory. Let us understand what are the differences and types of errors, defects, bugs, and incidents; and how they impact the cybersecurity arena.
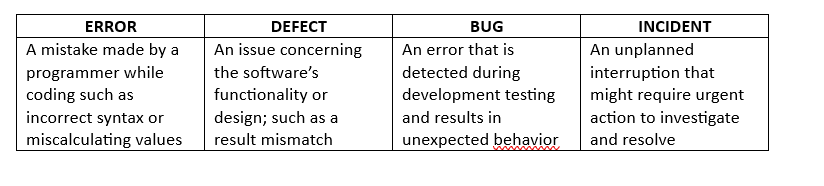
TYPES:
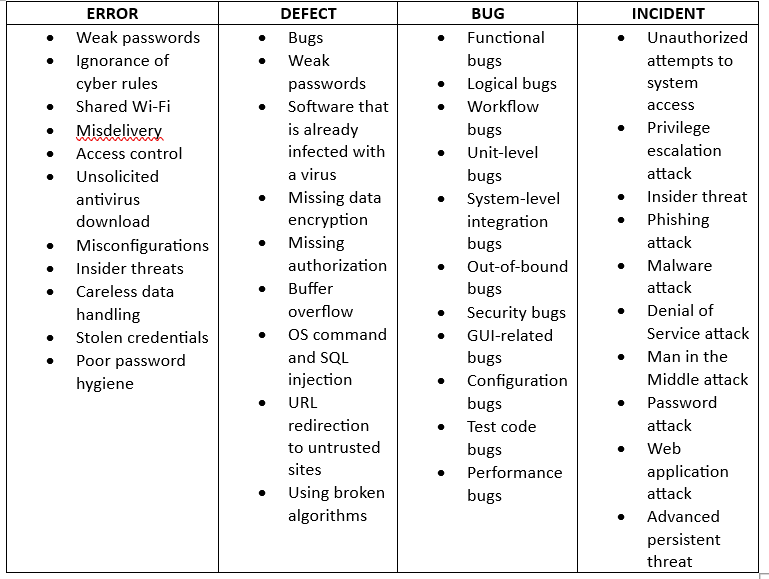
Best Practices to Reduce These Cybersecurity Attacks:
• Distributed load testing reveals potential latency issues and offers a consistent user experience globally
• Constant testing must become a part of your software development cycle to detect bugs and defects earlier
• Users and stakeholders must work closely with the developers to provide effective solutions
• Consider real-world user interactions to design realistic test scenarios
• Automated software testing must be deployed for lesser human involvement; drastically leveraging minimal chances of errors and bugs
Gaining an in-depth understanding of the types explored above is a must if you wish to take on a career stream in cybersecurity. Becoming a cybersecurity professional demands perseverance and top-notch cybersecurity skills to fight the cyberthreat menace like a pro!
How can a Cybersecurity certification help you?
World-class cybersecurity certification programs are designed in such a way that they accommodate every aspirant and assist them in building a career with the most futuristic cybersecurity skills on display. Some of the popular and globally trusted cybersecurity certifications; offered by the United States Cybersecurity Institute (USCSI®) can lead you to a thriving career beginning with a surefire about 40% raise in the expected salary. However, there are many other credentials, degrees, and courses doing the rounds. But, USCSI® is ranked among the elite pioneer providers of quality cybersecurity credentials worldwide. With their presence in over 160 countries worldwide; you are sure to get enrolled in the most suited cybersecurity certification programs; that are tailored to your skill requirement and resonate with your long-term cybersecurity career goal.
Cybersecurity is an ever-growing industry. With greater parts of the USA and other countries such as Texas, New Mexico, and Colorado (Cyberseek.com), among others brimming with meaty job roles for specialized cybersecurity professionals. You are sure to land your dream cybersecurity job with these credentials gracing your portfolio. Attend to the most recent developments in the cybersecurity threats landscape with much strength and skill with the best worldwide credentials on offer. You cannot deny the importance of these certification badges when they assure you a quick pick treatment against your competitors and set you a bar higher in the competitive arena. Make yourself available for big career gains with these core skills enhanced in the sphere of types of bugs, defects, errors, incidents, and other vulnerabilities; and incredibly targeted nuances to fight them.
Disclaimer: We do not promote, endorse, or advertise betting, gambling, casinos, or any related activities. Any engagement in such activities is at your own risk, and we hold no responsibility for any financial or personal losses incurred. Our platform is a publisher only and does not claim ownership of any content, links, or images unless explicitly stated. We do not create, verify, or guarantee the accuracy, legality, or originality of third-party content. Content may be contributed by guest authors or sponsored, and we assume no liability for its authenticity or any consequences arising from its use. If you believe any content or images infringe on your copyright, please contact us at support@indibloghub.com for immediate removal.
Copyright © 2019-2025 IndiBlogHub.com. All rights reserved. Hosted on DigitalOcean for fast, reliable performance.






