Identity and Access Management Market: Redefining Digital Identity Security
Strong 8k brings an ultra-HD IPTV experience to your living room and your pocket.
Introduction
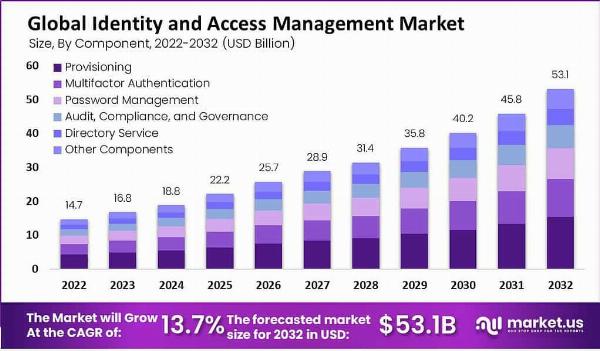
The Identity and Access Management (IAM) market is a dynamic sector driven by the need for enhanced cybersecurity and effective management of digital identities. The rapid digital transformation across industries, the surge in cyber threats, and increasing regulatory requirements are key factors propelling market growth.
Read More - https://market.us/report/identity-and-access-management-market/
With businesses seeking robust solutions to protect sensitive data and streamline user access, the IAM market presents significant opportunities. However, challenges such as integration with legacy systems, evolving cyber threats, and high implementation costs need to be addressed. New entrants can capitalize on opportunities by leveraging advancements in technology, exploring emerging markets, and offering innovative IAM solutions.
Emerging Trends
Artificial Intelligence and Machine Learning: The incorporation of AI and ML into IAM systems is revolutionizing the market. These technologies enhance threat detection capabilities, automate routine tasks, and provide personalized user experiences. AI algorithms can analyze vast amounts of data to identify unusual patterns and potential security breaches more effectively than traditional methods.
Cloud-Based IAM Solutions: The shift towards cloud computing is a major trend in IAM. Cloud-based solutions offer scalability, flexibility, and cost-efficiency, making them an attractive option for businesses of all sizes. These solutions also facilitate remote work and support the growing trend of hybrid and multi-cloud environments.
Zero Trust Security Models: The zero trust model is gaining traction as organizations move away from traditional perimeter-based security. This model requires continuous verification of user identity and access rights, regardless of the user’s location or device. It helps in mitigating risks associated with insider threats and compromised credentials.
Biometric Authentication: Biometric technologies, such as fingerprint, facial recognition, and voice authentication, are becoming increasingly popular. These methods provide a higher level of security and convenience compared to traditional passwords, making them a preferred choice for both consumer and enterprise applications.
Integration with IoT: As the Internet of Things (IoT) continues to expand, IAM solutions are evolving to manage access across a growing array of connected devices. Integrating IAM with IoT helps ensure that devices and users are properly authenticated and authorized, reducing the risk of unauthorized access and data breaches.
Top Use Cases
Employee Access Management: IAM systems are essential for managing employee access to organizational resources. They ensure that employees have the appropriate permissions based on their roles, thereby preventing unauthorized access and minimizing security risks.
Regulatory Compliance: IAM solutions play a crucial role in meeting regulatory requirements such as GDPR, HIPAA, and CCPA. They provide tools for managing access, tracking user activities, and generating audit trails to demonstrate compliance.
Customer Identity Management: For businesses with online services, managing customer identities securely is vital. IAM solutions help in creating and maintaining secure user accounts, enhancing the overall user experience while protecting sensitive customer information.
Single Sign-On (SSO): SSO solutions simplify the user experience by allowing access to multiple applications with a single set of credentials. This not only improves convenience for users but also enhances security by reducing the need for multiple passwords.
Privileged Access Management: Managing privileged accounts is critical for protecting sensitive systems and data. IAM solutions for privileged access management monitor and control the activities of high-privilege users to prevent misuse and minimize the risk of security breaches.
Major Challenges
Integration with Legacy Systems: Many organizations still rely on outdated systems that can be challenging to integrate with modern IAM solutions. This complexity can lead to higher costs and extended implementation times.
Evolving Cyber Threats: The constant evolution of cyber threats requires IAM solutions to be adaptive and continuously updated. Staying ahead of new attack vectors and techniques is a significant challenge for IAM vendors.
High Implementation Costs: The cost of deploying comprehensive IAM solutions can be substantial, particularly for small and medium-sized enterprises. This can be a barrier to adoption for some organizations.
User Resistance: Employees may resist new IAM systems if they perceive them as cumbersome or intrusive. Effective change management and user education are essential to ensure smooth adoption.
Data Privacy Concerns: Protecting sensitive identity data while complying with privacy regulations poses a challenge. IAM solutions must balance security with privacy to maintain user trust and meet legal requirements.
Market Opportunity
Growing Demand for Cloud Solutions: The increasing adoption of cloud technologies presents opportunities for cloud-based IAM solutions that offer scalability and flexibility to businesses.
AI and Automation Integration: Integrating AI and automation into IAM solutions can provide advanced security features and operational efficiencies, attracting businesses seeking to enhance their security posture.
Expanding Emerging Markets: Emerging markets are experiencing rapid digital growth, creating opportunities for IAM providers to offer solutions tailored to these regions.
Regulatory Changes: The ongoing evolution of regulations creates demand for IAM solutions that ensure compliance, presenting opportunities for vendors to develop solutions that address new compliance requirements.
IoT Growth: The expansion of IoT devices drives the need for IAM solutions that can manage access across a diverse range of connected technologies, offering opportunities for innovation and market growth.
Conclusion
The IAM market is on a growth trajectory fueled by digital transformation, increased cybersecurity concerns, and regulatory pressures. Emerging trends such as AI integration, cloud adoption, and zero trust models are shaping the future of IAM, presenting both challenges and opportunities.
While integration issues, evolving threats, and high costs are significant hurdles, there is considerable potential for innovation and growth. New entrants can thrive by developing cutting-edge solutions that address current market needs and align with evolving trends, capitalizing on opportunities in emerging markets and leveraging advancements in technology.
Note: IndiBlogHub features both user-submitted and editorial content. We do not verify third-party contributions. Read our Disclaimer and Privacy Policyfor details.


