What is CIS Compliance? A Practical Guide for Modern Businesses
Strong 8k brings an ultra-HD IPTV experience to your living room and your pocket.
In an era where cyber threats are becoming more sophisticated and data protection regulations are tightening, organizations can no longer afford to treat security as an afterthought. Enter CIS Compliance—a practical, widely respected standard designed to help businesses of all sizes secure their systems, data, and infrastructure.
But what exactly is CIS compliance? How does it help reduce risk and ensure robust cybersecurity hygiene?
Let’s break it down.
What is CIS Compliance?
CIS Compliance refers to aligning your organization’s IT systems and processes with the CIS Controls and CIS Benchmarks developed by the Center for Internet Security (CIS). These resources provide prescriptive, consensus-driven best practices for securing IT environments.
CIS Controls: A prioritized set of 18 critical security measures, known as the CIS Critical Security Controls (CIS Controls v8), designed to prevent the most common and damaging cyberattacks.
CIS Benchmarks: Configuration guidelines for securing specific technologies like operating systems, cloud platforms, databases, and network devices.
Achieving CIS compliance means your systems are configured to meet the security requirements outlined in these controls and benchmarks.
Why is CIS Compliance Important?
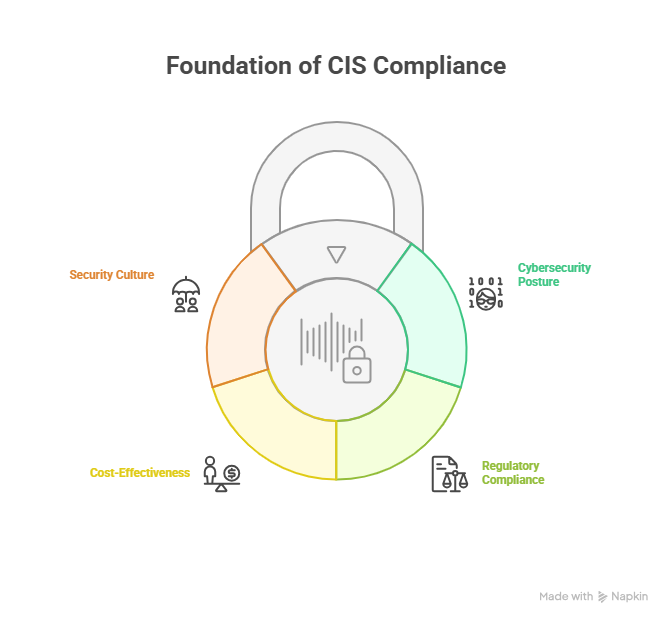
1. Strengthens Cybersecurity Posture
CIS provides actionable steps that organizations can implement to reduce their attack surface and mitigate risk effectively.
2. Supports Regulatory Compliance
CIS Controls often map to major regulatory frameworks like NIST 800-53, HIPAA, PCI-DSS, ISO 27001, and GDPR. Following CIS can streamline audits and demonstrate compliance readiness.
3. Cost-Effective and Scalable
Unlike some proprietary standards, CIS guidelines are free to access and scalable across businesses of any size—making it ideal for SMBs and enterprises alike.
4. Builds a Culture of Security
By embedding CIS into IT operations, organizations encourage a proactive, risk-aware mindset among their teams.
Who Should Care About CIS Compliance?
CIS compliance is especially important for:
- IT Teams managing infrastructure, cloud environments, and endpoints
- CISOs and Security Leaders building risk management programs
- SMBs looking for a structured yet practical way to improve security
- Enterprises needing to demonstrate due diligence and accountability
- Regulated Industries (healthcare, finance, education, government)
Key Components of CIS Compliance
1. CIS Controls v8
- 18 controls grouped into 3 implementation tiers: Basic, Foundational, and Organizational.
- Examples: Inventory and Control of Assets, Secure Configuration, Account Management, Continuous Vulnerability Management.
2. CIS Benchmarks
- Over 140 configuration guides for technologies like Windows, Linux, AWS, Azure, Cisco devices, and more.
- Each benchmark provides Level 1 (basic hygiene) and Level 2 (advanced security) profiles.
3. CIS-CAT Pro
- CIS Configuration Assessment Tool to scan, score, and report on system compliance with benchmarks.
4. Automated Tools
- Integration with tools like Ansible, Chef, and Puppet for implementing and enforcing benchmark configurations.
How to Get Started with CIS Compliance?
1. Evaluate Your Environment
Start with an inventory of your systems, platforms, and applications.
2. Download CIS Benchmarks
Visit cisecurity.org and access benchmarks tailored to your technologies.
3. Run a Baseline Assessment
Use CIS-CAT or compatible scanning tools to assess your current compliance posture.
4. Remediate Non-Compliance
Update configurations, disable insecure settings, and enforce strong access controls as per the benchmarks.
5. Monitor and Maintain
Build continuous compliance by integrating CIS checks into your patch management, configuration management, and security operations processes.
CIS Compliance vs. Other Frameworks
While frameworks like NIST, ISO, or COBIT offer governance and risk management guidance, CIS shines for its technical precision. It’s hands-on, concrete, and especially useful for teams looking to implement controls quickly.
Tip: Use mapping tools to align CIS Controls with your industry’s regulatory requirements.
Final Thoughts
CIS compliance is one of the most accessible and impactful ways to build a strong cybersecurity foundation. Whether you're starting your security journey or fine-tuning an existing program, the CIS Controls and Benchmarks provide a roadmap that’s practical, effective, and trusted worldwide.
Ready to secure your systems the right way?
Start by exploring the CIS Benchmarks or check out this post on CIS Hardening to dive deeper into system-level security.
Need help implementing CIS compliance across your devices?
Reach out to your IT partner or explore compliance automation solutions that can streamline assessment, remediation, and reporting.
Note: IndiBlogHub features both user-submitted and editorial content. We do not verify third-party contributions. Read our Disclaimer and Privacy Policyfor details.