Spear Phishing: How Cybercriminals Exploit Personal Information
Strong 8k brings an ultra-HD IPTV experience to your living room and your pocket.
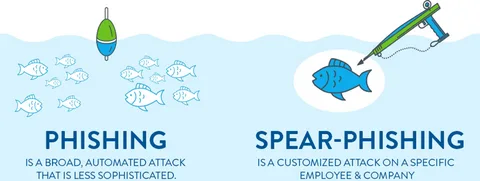
Spear phishing is one of the most focused and advanced forms of cyberattacks. Attackers typically rely on social engineering methods as a primary vector that ensures an attack will be successful. Spear phishing does not involve casting a wide net randomly, like spam or phishing, hoping to catch a fish. It is crafted and focused on how to take advantage of particular individuals or organizations, which makes them much more hazardous and difficult to spot. In this article, we are going to discuss the major role that social engineering plays in spear phishing and how cybercriminals use personal information to construct plausible attacks.
What is Spear Phishing?
It is vital to understand first what is spear phishing before looking at the role of social engineering in the same. Spear phishing is a kind of cyber attack wherein hackers send fraudulent communications, usually emails, but appear to originate from trusted sources. While regular phishing is a blind casting for victims, spear phishing targets only one individual or organization. The attacker does some research on their target and uses personal details to construct a message that will seem much more legitimate and believable.
Social Engineering in Spear Phishing
Social engineering spear phishing, in its very nature, is the manipulation of human behavior rather than technical vulnerabilities. Cybercriminals devise psychological strategies to trick the targeted victim into revealing sensitive information, clicking on malicious links, or downloading harmful attachments. This type of attack utilizes personal details like names, job titles, interests, and even social media activities to create authentic and relevant messages.
For example, the spear phishing email might come from an executive or trusted peer regarding some project at hand or some urgent issue. Even the service provider, say the IT company or bank, can impersonate the attacker to build pressure on the target and compel him to take immediate action. It's quite easy to get someone to fall into their scam by preying on those feelings: fear, curiosity, or even the desire to help.
What is a Spear Phishing Attack?
A spear phishing attack is a highly crafted attempt to deceive a targeted individual or organization into divulging sensitive data or performing some desired action that benefits the attacker. Attacks in this realm most often originate through spear phishing emails, which appear valid and are personalized with data captured from social media, previous interactions, or other publicly available sources. In influencing the victim to take action on the malicious message, the attacker might use many different social engineering techniques: a sense of urgency, trust, or familiarity.
For instance, the cybercriminal might disguise as an HR manager in a spear phishing email and ask the target to click on a link to "verify" personal information. The link forwards the target to a sham login page, which is actually there to pilfer the login credentials of the victim. Alternatively, the email will contain an infected attachment related to a very important document. When opened, the attachment installs malware in the system of the victim, whereby the attacker gains unauthorized access.
Spear Phishing vs. Phishing: The Critical Difference
One of the huge differences between spear phishing and normal phishing is personalization. While phishing sends out general emails to thousands in hopes of catching a few victims, spear phishing targets select individuals, often with information relating to the victim's life or work.
In phishing, it is usually a forged e-mail address, similar to an existing one; however, this method lacks a personal touch and context in contrast to spear phishing. Spear phishing emails, on the other hand, try to appear as close to reality as possible, using either the victim's name, job title, or even reference to specific events to increase their chances of success.
What Helps Protect From Spear Phishing?
Spear phishing requires awareness, vigilance, and the use of appropriate cybersecurity measures for prevention. Major steps in spear phishing protection involve education on the signs that indicate the possibility of a spear phishing attack. These include:
- Unsolicited requests for sensitive information
- Grammatically incorrect or oddly phrased e-mails
- Requests to click on suspicious links or to download attachments
- A sense of urgency or being pressured into immediate action.
Another important step is the legitimacy of unsolicited or suspicious requests. The latter can be validated through a personal approach to the person or company that apparently issued the email, by using contact details previously known to be trusted and never through direct reply to the mail in question.
Furthermore, advanced email filtering solutions combined with multi-factor authentication can reduce spear phishing susceptibility. Protection tools for spear phishing add an extra layer of detection and blocking capabilities for spear phishing emails even before they reach your inbox.
How to Prevent Spear Phishing: Some Best Practices to Safeguard Against It
Individuals and organizations can prevent spear phishing with a multi-layered approach to cybersecurity. Here are just a few of the best practices:
Employee and Individual Training: Training about how to identify spear phishing emails, among other social engineering attacks, is required. The employees should be instructed that when any suspect email comes to one's inbox, reporting it immediately is the best thing to do.
Keep Software Up-to-Date: Keep the operating systems of software, browsers, and security software up-to-date. Cybercriminals take advantage of people who don't update their software because the old versions have many vulnerabilities.
Anti-Phishing Technologies Implementation: Tools like email filters and web traffic monitoring software may prevent malicious emails and websites that can be used for cyber spear phishing attacks.
Use Strong Passwords and Multi-Factor Authentication: Strong passwords combined with MFA add layers of security, hence making it difficult for the attackers to get unauthorized access.
Verify Suspicious Requests: If an email asks for personal information or any activity out of the ordinary, do not take any action without the sender's confirmation.
The Cyber Spear Phishing Menace: An Increasing Trend
The spear phishing attacks continue to increase in their level of sophistication as cybercriminals find other ways of getting around traditional security measures. As technology continues to improve and more personal information becomes available online, the social engineering aspect of spear phishing will remain very effective. How individuals and organizations can stay informed and proactive about changing defense strategies is key in combating this evolving threat.
Understanding social engineering in spear phishing attacks, and making adequate precautions, is important for your further protection and your organization from becoming victims of such targeted attacks.
Note: IndiBlogHub features both user-submitted and editorial content. We do not verify third-party contributions. Read our Disclaimer and Privacy Policyfor details.