The Invisible Eavesdropper: Unmasking the Art of Sniffing in Ethical Hacking
Strong 8k brings an ultra-HD IPTV experience to your living room and your pocket.
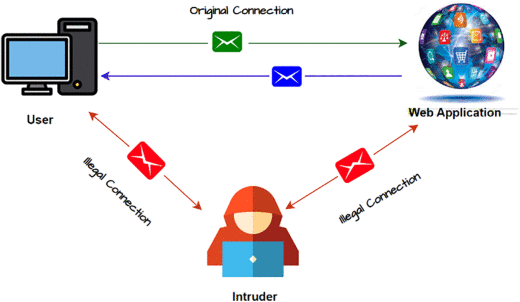
Ever wonder how information travels across the vast digital landscape? It might seem like magic, data packets zipping through invisible wires and airwaves to reach their destination. But like any journey, this digital voyage leaves traces, whispers in the wind that a skilled observer can intercept and understand. This is the realm of "sniffing," a fundamental technique explored within the curriculum of any comprehensive ethical hacking course.
At its core, is the art of capturing and analyzing network traffic. Imagine a detective meticulously listening in on conversations happening in a crowded room. Instead of voices, the ethical hacker intercepts data packets – the fundamental units of communication on a network. These packets contain a wealth of information, from website requests and email content to login credentials and sensitive financial details.
Now, before you envision shadowy figures lurking in dark corners, remember the "ethical" part of ethical hacking. In this context, it isn't about malicious eavesdropping for personal gain. Instead, it's a powerful diagnostic and security assessment tool. Ethical hackers learn sniffing techniques to understand network behavior, identify vulnerabilities, and ultimately, fortify digital defenses against real-world threats.
Think of it like a doctor using an X-ray to diagnose a hidden ailment. Sniffing allows ethical hackers to peer beneath the surface of network communication, revealing potential weaknesses that malicious actors could exploit. By understanding how data flows and what information is being transmitted in plain text or poorly encrypted, they can recommend and implement stronger security measures.
The curriculum of an ethical hacking course delves deep into the technical aspects of sniffing. You'll learn about various tools and techniques, from basic packet capture utilities to sophisticated protocol analyzers. You'll understand the intricacies of network protocols like TCP/IP, HTTP, and DNS, and how sniffers can dissect the headers and payloads of individual packets.
Imagine learning how to use Wireshark, a popular open-source network protocol analyzer. You'll be able to see the raw data being exchanged between devices on a network in real-time. You'll learn to filter and analyze this data, identifying patterns, anomalies, and potentially sensitive information being transmitted insecurely.
Furthermore, ethical hacking courses explore different methodologies. Passive sniffing involves simply observing network traffic without actively interacting with it – like our detective quietly listening. On the other hand, it involves injecting packets into the network to elicit responses and gain further insights – a more proactive investigative approach.
The implications of understanding these are profound. An ethical hacker armed with this knowledge can:
- Identify unencrypted sensitive data: Discover passwords, credit card details, or confidential communications being transmitted in plain text.
- Detect network anomalies: Spot suspicious traffic patterns that might indicate a malicious intrusion or attack.
- Troubleshoot network issues: Analyze communication breakdowns and identify the root cause of network problems.
- Assess the effectiveness of security controls: Verify if encryption protocols are properly implemented and if network segmentation is effective.
Mastering these techniques is a crucial step in becoming a proficient ethical hacker. It provides a fundamental understanding of how networks operate and the potential vulnerabilities that can exist within them. It's about understanding the invisible language of the digital world to protect it from those who seek to exploit its weaknesses.
Ready to unravel the mysteries of network communication and become a guardian of the digital realm?
Embark on your journey into the fascinating world of ethical hacking with Win in Life Academy's Certified Ethical Hacker (CEH) program. Our comprehensive curriculum will equip you with the knowledge and skills to not only understand techniques like these but also to effectively defend against them.
Click here to learn more and take the first step towards a rewarding career in cybersecurity:
Note: IndiBlogHub features both user-submitted and editorial content. We do not verify third-party contributions. Read our Disclaimer and Privacy Policyfor details.


